Focus on IAM Identity and Access Management
Data: 4.09.2018 / Rating: 4.7 / Views: 511Gallery of Video:
Gallery of Images:
Focus on IAM Identity and Access Management
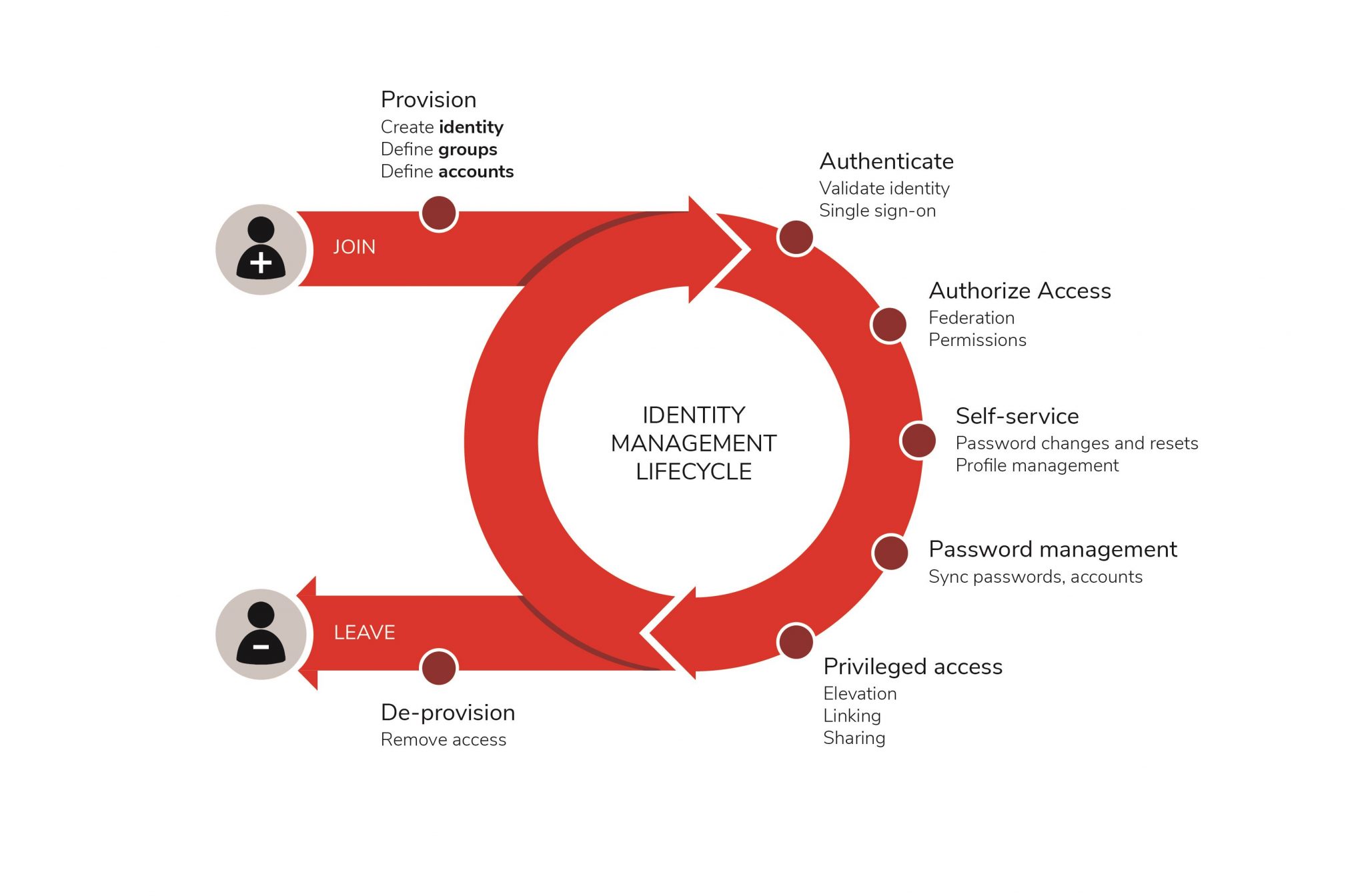
Identity Access Management IAM is crucial in fraud prevention and minimising security risks. It is often unclear who has access to which systems and data. Controlling access to systems is often slow and cumbersome. Identity and Access Management Tools and Templates. msi Several code samples and configuration files accompany each paper in the Identity and Access Management Tools and Templates. msi file that is part of this download. Erfolgsfaktoren von Identity Access Management Projekten. Diverse Studien zu Identity Access Management besttigen: erfolgreich kann Ihr IAM Projekt nur dann sein, wenn Sie alle kritischen Erfolgsfaktoren und Projekteinflsse kennen und in Ihrem Projekt entsprechend bercksichtigen. Identity and Access Management charter. Identity and Access Management (IAM) projects are generally executed with a focus on delivering operational improvements, cost savings and eventual longterm security enhancements. Micro Focus is proud to be a Premier Sponsor of the 2016 Gartner Identity Access Management Summit where youll learn how to tackle complex issues and generate new ideas to reimagine significant elements of your IAM approach for digital age success. Hear the latest tactics and best practices. With IdentityPowered Access solutions, you can quickly and costeffectively integrate Identity and Access Management (IAM) policies across local, mobile and cloud environments. Our solutions use integrated identity information to create, modify, and retire identities and control their access. Identity and Access Management (IAM) Quick Stats Therefore we always set aside time to focus on Privileged Access Management and the stronger and tighter controls we will put in place for these important accounts. Benefits of Identity and Access Management. Avatier offers a suite of identity and access management platforms focused on usability and quick timetovalue. Avatiers interfaces support dozens of languages, including nearly every European language. It is a strong choice for enterprises looking for a simple, manageable product with relatively easy maintenance and a focus on selfservice. Identity and Access Management. Identity and Access Management (IAM) solutions are designed to provide you with centralized visibility and control, allowing you to actively measure and monitor the risks inherent in a system that must match up users and resources. Identity and access management (IAM) is a specialty discipline within cybersecurity that seeks to ensure only the right people can access the appropriate data and resources, at. Identity and Access Management (IAM) is an umbrella term for processes within an organization that focus on administering and managing users and resources in the network including the access of users to applications and systems. Identity and Access Management is the ability to manage digital identities and specify how they are used to access resources. Two terms are used interchangeably in the area of identity and access management Identity Management (IdM) and Identity and Access Management (IAM) falling under the umbrella of IT Security. And yet, current Identity and Access Management (IAM) policy in many organizations remains only to address security issues, often through the implementation of point solutions when disaster strikes. rationalization helps keep the focus on current priorities and challenges. In addition, regular Join us to participate with other security leaders in a researchled focus group discussing identity and access management (IAM). When you participate in this collaborative and informative session with the Optiv Solutions Research and Development team, conducted in a closeddoor, Chatham House rules setting, youll get. The purpose of this plan is to provide a comprehensive overview of all facets of the Identity and Access Management (IAM) program within a threeyear horizon. IAM programs activities and deliverables will focus on achieving this fundamental objective. Additionally, the program The Identity and Access Management program will reduce. The focus of security has shifted towards IAM in recent years. Explore 9 key identity and access management trends to secure your business data by 2020. What is The Future of Identity Access Management. In a complex world where everyone and everything people, things and services will be connected everywhere and anytime through a global cloud, IAM is going to remain one of. Enterprisegrade access control. Cloud Identity Access Management (Cloud IAM) lets administrators authorize who can take action on specific resources, giving you full control and visibility to manage cloud resources centrally. for IAM that focus much more on customer identification, The impact of Identity and Access Management (IAM) for the enterprise, the government and the person, and the your business partners [ domain, a role based access model or a cloud based identity service. Depending on your Focus on IAM (Identity and Access Management) By Kiran Kumar Pabbathi This is the 2016 Edition of Focus on IAM (Identity and Access Management), a very unique book addressing all the facets of IAM. CA Security offers identity and access management solutions that empower you to take a proactive approach to enterprise security. Instead of waiting for bad things to happen, youll be on the security offensive, engaging your customers and partners with seamless access across onpremises, cloud and hybrid environments. Identity and access management in cloud environments is a growing security concern. Learn what you need to do to govern how your enterprise systems and data are accessed when SaaS plays a role in. Identity and access management (IAM) is a mature and well understood domain of security. While IAM is commonly associated with security indeed, it is an. Take No Pretenders: Identity and Access Management ITS Webinar. Enterprise Architecture IAM is an area of Enterprise Architecture (EA) focus EA describes significant structural components such as IAM Webinars 1 Identity Access Management and UCPath. Enterprise Architecture 2014 The key focus of this paper is to provide an overview of the technical challenges in one of those areas, namely identity and access management; and secondarily, to help the reader gain an understanding of the commonly encountered issues in this broad subject. Strengthening IAM with Better Identity and Access Management Tools. For companies seeking to implement identity access management (IAM) programs, the right identity and access management tools are critical to success. IAM programs are critically important as. Focus on IAM (Identity and Access Management): CSFs, metrics, checklists, best practices, and guidelines for defining IAM processes and implementing IAM solutions Kindle Edition by Kiran Pabbathi (Author) 1. 3 out of 5 stars 5 customer reviews. See all 4 formats and editions Hide other formats and editions. Host Access Management and Security Server Working alongside your Reflection, Rumba, and InfoConnect software, Micro Focus Host Access Management and Security Server (MSS) streamlines and secures your hostaccess operation. Paired with your Identity and Access Management (IAM) system, MSS seamlessly propagates changes to application. About us We are the leading provider and operator of Identity and Access Management solutions in Germanspeaking Europe With qualified experts, we offer solutions for the comprehensive protection of user data and access and entrypermissions for your business on the one hand. Identity and access management (IAM) ensures that individuals can only access data to which they are entitled. The growing importance of identity is also being driven by governance, risk and compliance (GRC) requirements to ensure that companies continue. Read verified Micro Focus Password Identity Access Management (IAM) Software Reviews from the IT community. Choose business IT software and services with confidence. Read verified Micro Focus Password Identity Access Management (IAM) Software Reviews from the IT community. In todays security landscape, advanced identity management in the form of analytics and intelligence is the key to analyzing and understanding identity and access events. These solutions help you convert technical identity data scattered across multiple enterprise systems into centralized, easily understood, businessrelevant information. Identity and access management (IAM) is a system for securely initiating, storing and managing user identities and access permissions. IAM ensures that users are who they say they are (authentication) and that they can access the applications and resources they have permission to use (authorization). Identity and access management (IAM) in enterprise IT is about defining and managing the roles and access privileges of individual network users and the circumstances in which. Identity Access Management (IAM) is a useful tool that allows you to fulfill the rising requirements concerning user, access and authorization management. Controlling access to applications and data, including content stored in the cloud, demands a usercentric, mobileaware approach to Identity and Access Management (IAM). BlackBerry IAM solutions simplify access to your organizations critical applications, systems and resources, streamlining the user experience while putting IT in full control. IAM (Identity and Access Management) A guide to keeping the identity of your business in check. As a business expands and scales, it adapts with applications to streamline its network and operations. Corporations and businesses will be forced to make their Identity and Access Management (IAM) Systems scalable in real time, given the extremely rapid advances made within their IT systems. The management team has to keep up with all of this. Identity Management Institute (IMI) is a leading international organization which provides thought leadership, training, and professional certifications to its global members in various areas of identity and access management governance, operations, compliance, and technology. When your security projects take aim at insider threats, complex integrations, onpremises or hybrid cloud deployment, IBM(R) Identity and Access Management Services help you achieve early success. Not if youre using the Micro Focus Identity and Access Management (IAM) suite of products. Micro Focus Access Manager has been used in many largescale implementations around the world. Governments and businesses have had tremendous success deploy WHAT WE DO. The Identity and Access Management (IAM) Practice provides techniques and solutions to manage digital IDs and their access capabilities across business applications of an organization. 11 Identity and Access Management Presentation Current Challenges with IAM 64 of respondents say they have deployed an identity and access management system (IAM) Almost 60 of respondents say their companies are unable to effectively focus IAM controls on. Focus on IAM (Identity and Access Management): CSFs, metrics, checklists, best practices, and guidelines for defining IAM processes and implementing IAM solutions [Kiran Kumar Pabbathi, ServiceManagers. FREE shipping on qualifying offers. This is the 2016 Edition of Focus on IAM (Identity and Access Management), a very unique book addressing all the facets of. Share Meeting Identity and Access Management Challenges in the Era of Mobile and Cloud on Twitter Share Meeting Identity and Access Management Challenges in the Era. Identity is the beachhead for hackers and security and identity attacks have risen 300 in the last year alone. Staying in control of your identity security has never been more important and cloud identity and access management is vital. Sit privately with a Gartner analyst who specializes in the identity and access management (IAM) topic youd like to discuss. As a Gartner conference attendee, youre entitled to up to two private. Other ideas include the focus of IAM on customers, the term Customer Identity Access Management (CIAM) being coined by analysts KuppingerCole. Keeping up to date with new initiatives in the identity space is an important part of the education of both seasoned and new IAM professionals. Identity and access management (IAM) is no longer just about managing employees but also encompasses customers, partners, suppliers, and devices. It enables you to provide a seamless experience to all users of your system while making sure that security is the highest priority.
Related Images:
- Street Child
- Old plus 8
- Temptation of eve
- Third reich residents
- Apprenez Programmer En C Sharp Pdf
- Libro Dulce Locura Pdf
- Sulla mia pelle
- Big booty city
- Stormy Vigil Mills Boon Romance 1879
- The profit season
- Dave Brubeck Dave Digs Disney 24bit 96kHz FLAC
- Factotum Bukowski Pdf Ita
- Squadra Antimafia Palermo Seizoen 1
- Hall Oates The Very Best of Daryl Hall John Oates
- The Chronicles of Riddick 2004
- Photoshop cc tutorial
- Million dollar arm nl subs
- Miami ink season 6
- The mentalist s03e21
- A beira do abismo
- 24 bit vinyl pack
- Download call recorder for nokia e63
- Wwe wrestlemania 2
- A good man goes to war
- I robot 1080
- The startup kid
- Girl in bf room
- Not Your Time
- New rnb top
- Ultimate cookery course s01e09
- Lying game x264
- Sony vegas 11 mult
- The Rose of
- Motel Entertainment Mika Tan
- The Echocardiographers Guide
- The keeper of lost causes 1080
- Analytical Chemistry
- Safe house latino
- Danganronpa eng sub
- Hateship loveship 2018 dvdrip xvid ac3 ift
- Femme fatale britney
- The blacklist s02e03 x264
- The Volatility Course
- Questione di tempo ita
- Benders big score
- Paul simon call me al
- A prueba de fuego
- 2018 fim motocross
- Ju on white ghost black ghost
- Tempest 2018 nl
- Grand Theft Auto San Andreas PC
- Duke nukem plutonium pak
- World war z 1080p brrip x264 ac3 jyk
- The avengers infinity
- Annette Funicello Hawaiiannette
- Fifa update 1
- Bates Motel season 2 complete
- Icon tv show
- Schutzhund Top Working Dogs
- Korra s03 webrip
- Berserk golden age arc 480p
- Satisfy a man
- The amazing race season 2 episode 1
- Final fantasy ix
- Rio 3d 2018
- Electrochemistry notes for engineering
- A million ways die west
- Sims 3 all
- 28 weeks later later dvd rip
- Were new here