Hacking wireless networks
Data: 1.09.2018 / Rating: 4.6 / Views: 740Gallery of Video:
Gallery of Images:
Hacking wireless networks
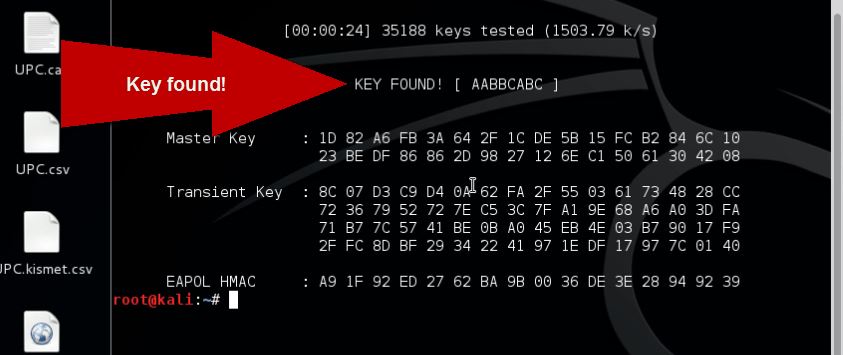
Wireless networks are convenient and popular, but poor configuration and encryption leave them open to attack. Hackers can use WiFi vulnerabilities to infiltrate your entire network. ShortDescription: In this course, youll learn the hacking methods that can be used to gain access to your network and how to best lower that security risk. Chapter 10 from the book Hacking Wireless Networks For Dummies by Kevin Beaver and Peter Davis covers installing and using network discovery and wardriving tools Kismet and Wellenreiter and discusses wardriving countermeasures. I am just trying to spread knowledge and info to people, and in this process I also learn. Hacking Wireless Networks For Dummies by Kevin Beaver, Peter T. Davis Become a cyberhero know the common wireless weaknesses Reading a book like this one is a worthy endeavor towardbecoming an experienced wireless security professional. In this course we look at hacking wireless networks, the associated tools and techniques used, and mitigation strategies. This course is the thirteenth in a series of courses which can used in preparation for the Certified Ethical Hacker exam. Do you want to setup your own hacking lab and learn through practice? If yes, then this is the book for you! Hacking Wireless Networks The ultimate handson guide, is a book written for people who seek to practice the techniques of assessing the security of wireless 30 real life scenarios and more than 300 figures the. Please put these essential wireless hacking tools to safe, legal and ethical use. Locating a wireless network is the first step in trying to exploit it. There are two wireless hacking tools that are commonly used in this regard. Start studying Hacking Wireless Networks. Learn vocabulary, terms, and more with flashcards, games, and other study tools. How to hack UPC wireless networks and other WLAN. If youre interested in learning more about WiFi hacking, penetration testing and wireless in general, you can follow any of these online courses: Online Hacking Courses. Learn Wifi HackingPenetration Testing From Scratch. In this Top 10 Wifi Hacking Tools we will be talking about a very popular subject: hacking wireless networks and how to prevent it from being hacked. Wifi is often a vulnerable side of the network when it comes to hacking because WiFi signals can be picked up everywhere and by anyone. Wireless networks are convenient and popular, but poor configuration and encryption leave them open to attack. Hackers can use WiFi vulnerabilities to infiltrate your entire network. An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as WiFi) can be found everywhere! If you have a PC with a wireless network card, then you must have seen many networks around you. Sadly, most of these networks are. Reaver is one of the best and effective tool for hacking wireless networks available. To use reaver, you have to install Kali Linux on your system. Kali Linux is an Operating system and Reaver is. Hacking Wireless Networks A wireless network refers to any type of computer network that is wireless and is commonly associated with a telecommunications network whose interconnections between nodes are implemented without the use of wires. Many wireless routers have a setting that allows you to administer the router via a wireless connection. This means that you can access all of the routers security settings and other features without having to be on a computer that is plugged into the router using an Ethernet cable. Wireless networks are so convenient not only for you, but also for those nefarious types who'd like to invade them. The only way to know if your system can be penetrated is to simulate an attack. This book shows you how, along with how to strengthen any weak spots you find in your network's armor. go to the WiFi settings, turn on the wireless networks, and assign strong but easytorecall passwords. Wireless Networks and Hacking Wireless networks are based on IEEE 802. 11 standards defined by IEEE(Institute of Electrical and Electronics Engineers) for ad hoc networks or infrastructure networks. Infrastructure networks have one or more access points which coordinate the traffic between the nodes. Hacking Wireless Networks The ultimate handson guide, is a book written for people who seek to practice the techniques of assessing the security of wireless infrastructures. Through 30 real life scenarios and more than 300 figures the book In this video I show you how to hack a wireless network that's encrypted with a WEP key. We will be using Windows 7 and Linux. This method works on Windows Vista and XP as well. Hacking Wireless Networks Theory and practice English Size: 787. 4 MB Category: Video Training Before we begin: the practical use of the course you are going to see has been proven by thousands of people all over the world beginners and computer geeks as well. org item description tags) Ethical Hacking Wireless Hacking. Wireless networks are widely used and it is quite easy to set them up. A wireless router is the most important device in a wireless network that connects the users with the Internet. Ethical Hacking and Countermeasures. Version 6 Module XX Hacking Wireless Networks Module Objective This module will familiarize you with: Concept of Wireless Networking Effects of Wireless Attacks on Business Types of Wireless Networks Wireless Standards Antennas Wireless Access Points SSID Setting up a WLAN Detecting a Wireless Network How to Access a. Ethical Hacking: Hacking Wireless Networks By Dale Meredith In this course, you'll learn the hacking methods that can be used to gain access to your network and how to best lower that security risk. Hacking on computer networks is often done through scripts and other network software. These speciallydesigned software programs generally manipulate data passing through a network connection in ways designed to obtain more information about how the target system works. Hacking Techniques in Wireless Networks. Department of Computer Science and Engineering Wright State University Dayton, Ohio This article is scheduled to appear in The Handbook of Information Security, Hossein Bidgoli (EditorinChief), John Wiley Sons, Inc. Hacking Wireless Networks The ultimate handson guide, is a book written for people who seek to practice the techniques of assessing the security of wireless 30 real life scenarios and more than 300 figures the book examines in details the following areas: Discovery and Profiling of wireless networks Denial of. Your WiFi network is your conveniently wireless gateway to the internet, and since you're not Read more Read Today we're going to run down, stepbystep, how to crack a WiFi network with WEP. Hacking Wireless Networks for Dummies is a terrible book. If you are a regular person with social skills you have likely noticed that computer guys do not know how to communicate. Wireless networks are so convenient not only for you, but also for those nefarious types who'd like to invade them. The only way to know if your system can be penetrated is to simulate an attack. This book shows you how, along with how to strengthen any weak spots you find in your network's armor. In this video I show you how to crack wireless networks that are encrypted with WPA and WPA2 The Linux Operating System Built for Hacking Duration: 12: 36. Eli the Computer Guy 657, 667 views. programs for hacking wireless networks for pc free download How to Hack Wireless Networks, Actiontec 54Mbps Wireless PC Card, Bullant Remote for Pocket PC, and many more programs. The author does not have any responsibility if the attacking techniques that are described are used to gain unauthorized access or cause any damage to wireless networks. Here Download Also Module and Lab PDf File. Heres how attackers crack encrypted wireless networks. This isnt a how to crack a wireless network guide. Were not here to walk you through the process of compromising a network we want you to understand how someone might compromise your network. Cracking WiFi passwords isn't a trivial process, but it doesn't take too long to learnwhether you're talking simple WEP passwords or the more complex WPA. Learn how it works so you can learn. Wireless Tools Recommended WiFi Hacking Software For 2017 Wifiphisher is a WiFi hacking tool that can execute speedy automated phishing attacks against Wireless WiFi networks with the intention of discovering user and password credentials. The difference with this wireless tool (compared with the others) is that it launches a Social. Here is a collection of Best Hacking EBooks PDF 2018. Download Hacking Books In PDF and learn best hacking tutorials 2018. There are many ways to Learn Ethical Hacking like you can learn to hack from online websites, learn from Hacking books. Before we begin: the practical use of the course you are going to see has been proven by thousands of people all over the world. 'All wifi networks' are vulnerable to hacking, security expert discovers Many wireless routers are infrequently if ever updated, meaning that they will continue to communicate in an insecure. How to Secure wireless networks; Hacking Activity: Crack Wireless Password What is a wireless network? We will also provide useful information that can be used to crack the WEP and WPA keys of wireless networks. Decoding Wireless network passwords stored in Windows. A developer named Arnau from Spain has released a new project called CoffeeMiner that is designed to hack wireless networks to inject cryptocurrency mining code inside connected browsing sessions. CoffeeMiner project use the power of maninthemiddle attack to inject some javascript code in the. Understanding Wireless Hacking Hacking a wireless network is not much different from hacking a wired LAN Techniques for hacking wireless networks Port scanning Enumeration 76. Tools of the Trade Equipment Laptop computer A wireless NIC An antenna Sniffer software Back Track is the attack platform of choice for many Ethical Hackers and information security professionals. in ECCouncil iLabs, Backtrack is provided as a tool rich operating system for leading attacks and exploits. The wireless network is one of such new things, which began to catch on around the world due to its application on mobile platform. What this book Hacking Wireless Networks For Dummies pays close attention to is the wireless networks security problems, its purpose is to make you grow from a novice to an experienced wireless security. Before we address the hardware necessary to hack wireless networks, let me once again recommend the Aircrackng suite of hacking tools. Nothing else in our opensource world quite compares to the power and versatility of Aircrackng. A fast multicore or multiprocessor CPU is certainly helpful
Related Images:
- Power generation operation and control 3rd edition
- Cooking with s
- Photon Golf Digital Scorecard Manual
- Nicky romero vs krewella legacy
- Netcraft site report
- Maken ki two mp4
- Eye Candy Season 1 Complete
- Perfect body xxx
- Enemy the weekend
- The ashes 2018
- Walt kelly pogo
- The war at home series
- Reservoir Dogs 1992 swesub
- SALAS DE VENTAS Automotores Llano Grande
- Chicks same time ana
- I Can Make You Happy By Paul Mckenna
- A state of trance 600 expedition
- Watch what happens live teresa and joe
- Chris rea stoney road
- Arturia VOX Continental V
- Taylor swift best
- Blueprint 3d apk
- Bleach raw fade to black
- Nba 04 11 2018 heat
- Yves larock rise up
- Manuale Istruzioni Cordless Brondi Nice
- Person of interest S03E01 eztv
- English german pdf
- Fifa 07 xbox
- Call of Duty Black Ops Call
- The 100 s01e13 nl subs
- The black sails s01e01
- Beverly hills 90210 s01
- Rise of the legend
- Subtitles of her
- Duke of Hazzard 2018
- Planet asia nl
- Los singles hombres g
- Mathpower Seven Answers Chapter 1
- The game s01e01 720p
- Kanun keseksaan akta 574 PDF
- Demi lavato demi
- Branz good tiling practice guide
- Dual boot ubuntu
- One piece 91
- Printlock keygen serial
- The day of the future past
- Assassins creed 2 crack uplay download
- Shriman yogi marathi ebooks free download
- The Hacker Playbook
- FileCenter Professional
- Wow worship 1999
- Limitless 2018 dvd
- Fin and j
- Spill Prevention Control And Countermeasures Spcc
- Dll suite serial
- The mentalist season
- 2018 dragon eyes
- Bron s02e10 720p
- Massari be easy
- The bell witch haunting yify
- The Sitter 2018
- Britney Spears Interview
- Walter dean myers
- Desire mirror mirror
- Eyeon fusion x64
- Tatou Le Matou Cahier D
- Would i lie to you s03e01
- Britney spears music
- Snitch linfiltrato 2018
- Ableton live 9 suite 64
- Lultima estate
- White girl with round
- Year 7 Comprehension Exam Quizzes
- Free ride bike
- 30 Days To Understanding The Bible Free Pdf
- The dark flynn
- La noire de
- Call of duty 2 download highly compressed game
- Present perfect and past simple free worksheets
- Violette Opening Violette
- Witches of east end 1
- Imaginacion y Creacion en la Edad Infantil
- Lultima estate
- Sons of Anarchy Season 2
- Jetking networking books free download
- Windows 8 64
- Magic mike bdrip